Written By Angela Garfinkel, an industry expert with 30+ years of experience
In recent years, robocalls and nuisance calls have become a significant problem for consumers and the telecom industry. To address this issue, the Federal Communications Commission (FCC) and the Federal Trade Commission (FTC) launched an initiative to develop a technical standard that would enhance the security and authenticity of telephone calls. This led to the development of the STIR/SHAKEN framework. STIR (Secure Telephony Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using tokens) are technical standards that provide a secure framework for call authentication and verification. With authentication and verification in place, regulators can trace any call back to its origin almost immediately.
The rise of internet-based telephone and Voice over IP (VoIP) technology had made it difficult for authorities to track down and prosecute individuals involved in illegal robocalling activities. These calls are often made using spoofed Caller ID & IP information, making it challenging to identify the origin of the calls.
ROBOCALL VOLUMES
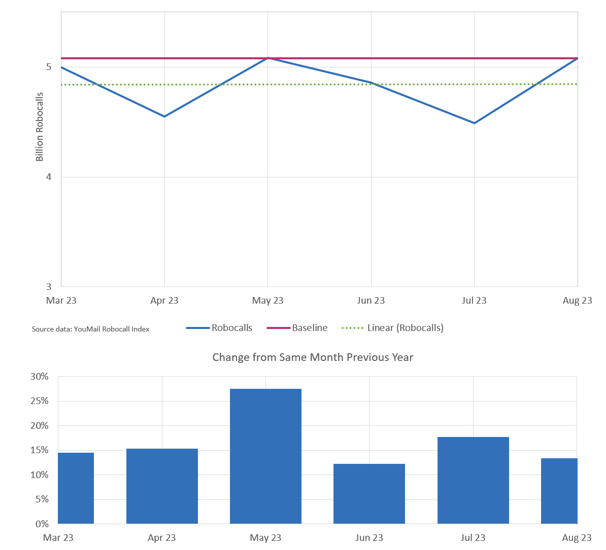
Source: Transnexus, Updated August 2023
STIR
STIR is a set of technical protocols that enable the authentication of call originators. It works by adding a digital signature, or token, to every call, identifying the originating telephone carrier, containing “NAM” Caller ID name information, in some cases, the reason for the call & calling parties logo. The digital signature allows for traceability and accountability, making it easier for regulators to track down illegal callers.
The STIR (Secure Telephony Identity Revisited) protocol is a key component of the STIR/SHAKEN framework. It works by adding a digital signature or token to telephone calls to ensure their authenticity and integrity. Here's a more detailed explanation of how STIR works:
1. Call Origination: When a call is initiated, the originating service provider (telephone carrier) generates a unique digital signature for that call. This signature includes information about the call, such as the calling party's identity and the called party's identity.
2. Certificate Authorities: The digital signature is based on cryptographic algorithms and is created using a private key owned by the originating service provider. To ensure trust and authenticity, the service provider obtains a digital certificate from a Certificate Authority (CA). The CA verifies the identity of the service provider and issues the certificate, which contains the public key corresponding to the private key used for signing calls.
3. Signaling and Transmission: The digital signature is then transmitted with the call as part of the signaling information. It travels along with the call as it traverses the telecom network.
4. Verification: When the call reaches the terminating service provider (the carrier of the called party), the digital signature is extracted from the signaling information. The terminating service provider uses the public key from the originating service provider's certificate to verify the authenticity of the signature. If the verification is successful, it confirms that the call originated from a legitimate source.
5. Attestation and Call Handling: Based on the result of the verification, the originating service provider assigns an attestation level to the call: A-level, B-level, or C-level. A-level attestation means the call is authenticated and can be trusted. B-level attestation means the caller is known, but there may be some uncertainty regarding the Caller ID number being used. C-level attestation means the call could not be authenticated or has passed through a gateway without proper authentication.
6. Call Handling Policies: The terminating service provider can then apply call handling policies based on the attestation level. For example, calls with A-level attestation can be allowed to go through without any restrictions, while calls with B-level or C-level attestation may be subject to additional scrutiny, such as being labeled as potential spam or blocked altogether.
By implementing the STIR protocol, telecom carriers can ensure the authenticity and integrity of telephone calls, making it more difficult for fraudulent or illegal robocalls to go undetected.
SHAKEN
SHAKEN complements STIR by providing call parties with the ability to decide how to handle calls based on their authentication status. Calls with valid signatures (attestations) are allowed to go through, while unsigned or improperly signed calls can be blocked or labeled as potential spam.
SHAKEN (Signature-based Handling of Asserted information using tokens) plays a crucial role within the STIR/SHAKEN framework by providing call parties with the ability to decide how to handle incoming calls based on their authentication status.
1. Attestation Levels: Under SHAKEN, calls are assigned attestation levels to indicate their authentication status and level of trustworthiness.
- A-Level Attestation: This is the most desirable level of attestation. It signifies that the call originator is known and authorized to use the displayed Caller ID information. A-Level Attestation provides the highest level of trust and confidence in the call's authenticity. Calls with A-Level Attestation are more likely to go through and be accepted by the call party.
- B-Level Attestation: B-Level Attestation indicates that the call originator is known, but there may be limitations or questions regarding their authorization to use the Caller ID information. While calls with B-Level Attestation may still go through, the level of trust and acceptance might be lower compared to A-Level Attestation.
- C-Level Attestation: C-Level Attestation is assigned to calls that pass through a gateway or intermediary without proper authentication. Calls with C-Level Attestation have the lowest level of trust and may raise suspicions about their legitimacy. The call party may choose to block or label such calls as potential spam or fraud.
2. Call Handling: Based on the assigned attestation level, the call party's telephone carrier can determine how to handle the incoming calls.
3. Acceptance: Calls with A-Level Attestation, indicating a high level of trust and authenticity, are likely to go through and be accepted by the call party. These calls are recognized as legitimate and authorized.
4. Blocking: Calls that lack proper authentication or have a C-Level Attestation may be blocked by the call party's telephone carrier. This helps prevent illegal or fraudulent calls from reaching the call recipient.
5. Labeling: In some cases, calls with B-Level Attestation or other suspicious attributes may be labeled as potential spam or fraud. This labeling provides a warning to the call recipient, allowing them to make an informed decision on whether to answer the call.
By implementing SHAKEN, the STIR/SHAKEN framework enables call parties to have greater control over the calls they receive. The attestation levels help them differentiate between legitimate calls and those that may be illegal or fraudulent. This ensures a more secure and trustworthy calling experience for consumers, improving their ability to identify and avoid unwanted or malicious calls.
Attestations
Attestations play a crucial role in the STIR/SHAKEN framework as they determine the level of trust and authentication associated with a call. Under the STIR/SHAKEN framework, calls can have three types of attestations: A-level, B-level, and C-level.
The attestation level of a call is determined by the originating telephone carrier. When a call is initiated, the originating carrier is responsible for assigning the appropriate attestation level based on their knowledge and verification of the caller's identity and authorization to use the displayed Caller ID information.
The originating carrier applies a set of criteria and checks to determine the attestation level. This may involve conducting a thorough Know Your Customer (KYC) process, verifying the legitimacy of the caller, and ensuring that they have the proper authorization to use the Caller ID.
Different carriers may have their own policies and procedures for assigning attestation levels. While there are guidelines and standards set by the STIR/SHAKEN framework, the specific implementation and decision-making process can vary among carriers.
Ultimately, the originating carrier's determination of the attestation level influences how the call is treated by other carriers, call parties, and analytics engines within the network. Higher attestation levels, such as A-level, generally carry more trust and credibility, while lower levels, such as B-level or C-level, may be subject to additional scrutiny, blocking, or labeling.
Robocalls by Attestation Levels
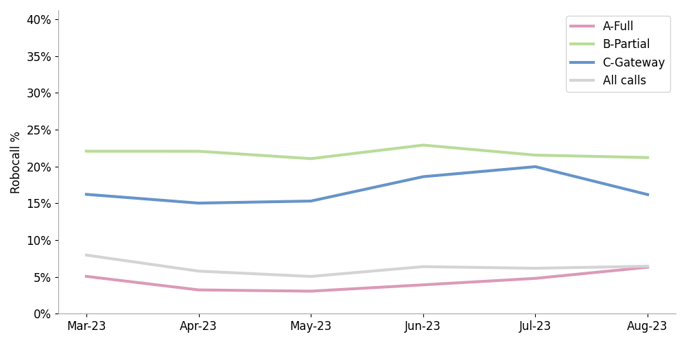 Source: Transnexus, Updated August 2023
Source: Transnexus, Updated August 2023
STIR/SHAKEN Timing & Milestones:
- August 2016: Task Force is created on the request of FCC Chairman Wheeler to “develop an action plan for providing consumers with robust robocall-blocking solutions.” This task force included members from some of the world’s largest companies like Apple, AT&T, Verizon, & TMobile.
- October 2016: Task Force releases their first public report.
- July 2019: The Federal Communications Commission (FCC) set a deadline for all carriers in the United States to implement the STIR/SHAKEN framework by July 2021. This deadline served as a strong push for carriers to adopt and implement the necessary technical standards.
- December 2020: The FCC issues “Caller Id Authentication” Best Practices guidance.
- June 2021: STIR/SHAKEN Broadly Implemented (report)
- December 2021: FCC Shortens implementation requirement deadline for small voice-service providers (<100k subscribers) from June 2023 to June 2022.
- October 2022: FCC Chairwomen Jessica Rosenworcel issues a public statement with forward looking statements about needs to address the definition of autodialers regarding the TCPA, expanding the Commission’s ability to track the businesses that entities scammers set up, and improving the FCC’s ability to pursue fines in court as opposed to relying on the DoJ.
- March 2023: FCC enhances & expands provider obligations to implement STIR/SHAKEN framework. The new rules will require intermediate providers that receive unauthenticated IP calls directly from domestic originating providers to use STIR/SHAKEN to authenticate those calls.
- May 2023: FCC releases clarifying statements that all carriers must respond to traceback requests within 24 hours, and require all carriers to know their upstream providers for every carrier in the call path.
Importance of Know Your Customer (KYC)
To ensure the effectiveness of the STIR/SHAKEN framework, carriers require their customers, especially call originators, to go through a Know Your Customer (KYC) process. It involves verifying the identity and legitimacy of call originators, ensuring they are authorized to use specific Caller ID information. Failure to provide this information may lead to calls being labeled or blocked.
The Importance of KYC in the STIR/SHAKEN Framework
1. Building Trust and Compliance: KYC builds trust and confidence between call originators and carriers by demonstrating a commitment to operating within legal and ethical boundaries. It aligns with regulatory requirements and promotes transparency, fostering a trusted relationship in the telecommunication industry.
2. Mitigating Risks: By verifying the identity and legitimacy of call originators, carriers can minimize the risk associated with fraudulent or illegal activities. The KYC process ensures that only authorized entities are allowed to use specific Caller ID information, safeguarding consumers and maintaining the carrier's reputation.
3. Enhancing Caller Reputation: Through the KYC process, carriers can verify the authenticity and credibility of call originators. This verification process helps establish the caller's reputation, ensuring that their calls are recognized as legitimate and increasing the chances of successful call delivery without being labeled or blocked.
What Carriers Need to Do to Perform KYC:
Here's a breakdown of what carriers typically need to do:
- 1. Develop Comprehensive Policies: Carriers need to establish clear KYC policies and procedures aligned with regulatory guidelines and industry best practices.
Collect Required Information: Carriers should gather specific information from call originators, including company details, contact information, tax identification numbers, and any licenses or registrations - 2. Verify Beneficial Ownership: It's essential to verify the ultimate beneficial owners (UBOs) of the call originator's business. UBOs are individuals who own or control a significant percentage of the company. Carriers may require supporting documentation for this verification.
- 3. Conduct Due Diligence Checks: Carriers should conduct due diligence checks to ensure compliance with regulatory requirements and ethical standards. Background checks and reputation assessments can help mitigate risks.
- 4. Maintain Documentation: Carriers must maintain accurate records of the KYC process, including the information collected, verification results, and supporting documents. These records serve as evidence of compliance and are crucial for audits and regulatory purposes.
- 5. Consider Third-Party Verification: In some cases, carriers may engage third-party entities, such as law firms or auditors, to perform independent verification. These third parties enhance the credibility and reliability of the KYC process.
- 6. Implement Ongoing Monitoring: Carriers should establish mechanisms for ongoing monitoring of call originators, detecting any changes in their business structure or ownership that may impact their legitimacy. Regular reviews and reassessments help ensure continued compliance.
How to avoid “Spam Likely” designation by carriers?
Read our post on “Stir Shaken Plus Intelligence” which outlines the importance of avoiding Recycled Caller Id Numbers, Single Number High Dialing Velocity, Improving ALOC (average length of call), and avoid using Dialers in the wrong situations.
Our Thoughts
STIR/SHAKEN regulation is a significant step forward in combating illegal robocalls and improving call authenticity. The framework provides a secure method of call authentication and verification, allowing carriers and regulators to identify and take action against illegal callers. By complying with the STIR/SHAKEN framework and working with authorized shaken service providers, call originators can improve contact rates and avoid being labeled or blocked.
In a public memo on October 27th, 2022, FCC Chairwoman Jessica Rosenworcel said “Scam artists are always looking for an angle. Those behind illegal robocalls are no exception. When we shut down one way for them to make these annoying calls, they look for another. So we have to be just as relentless. We need to be just as inventive using the tools we have to bring these junk calls to an end."
About Quality Voice & Data, Inc.
Founded in 2010, Quality Voice & Data, Inc. offers secure and reliable cloud-based telecom switching and VoIP services for customers nationally. This includes local Caller ID numbers, IVR, PBX, SMS & MMS messaging, Conference Calling, Monitoring & Remediation services, and SIP trunking with Shaken Attestation. Our Trusted Call Completion™ service is known for maximizing our customers' answer rates and protecting their reputation.
—
Written by Angela Garfinkel
Angela Garfinkel currently serves as a Director for Quality Voice & Data. With 30+ years of call center and business process outsourcing experience, Angela provides the QVD team with key insights to support product development, marketing and sales. In addition, Angela teams up with Dean Garfinkel for strategic planning and leadership development. In addition to founding Quality Contact Solutions in 2007, Angela also co-authored an online course for The Direct Marketing Association (DMA) called Teleservices. Angela’s formal educational background includes a Masters in Business Administration and an undergraduate degree in Telecommunications Management from the University of Nebraska.
Angela Garfinkel, Director at Quality Voice and Data, brings over 30 years of experience in call center and business process outsourcing. Well known in the telemarketing and telecommunications industry, she co-authored a course for The Direct Marketing Association and actively participates in professional groups like PACE. Her educational background includes an MBA and an undergraduate degree in Telecommunications Management from the University of Nebraska.
.jpg)